The ZeroLock® Management Console (ZMC) includes a set of default lockdown rules to ensure security. Many known exploits are covered with this “Recommended Rules” ruleset and outlined in the rule's description.
The latest ruleset is automatically added to the database when you first install the ZMC. The ruleset is protected and may not be changed but may be copied, allowing you to create and modify a ruleset based on your organization’s particular requirements.
Order Matters
The Recommended Ruleset is of the Ordered Rule Type, meaning that Lockdown rules (File Access, Network Access, and Program Execution rules) are evaluated top-to-bottom, with rules on top resolving actions before moving on to later rules down the chain.
Similar to a firewall, if an action matches a lockdown rule that is at the top of the list, it will take the actions specified for that rule and stop evaluating any rules below it. If it does not match, it will pass to the next rule in line until it matches. If no rules match, then the action is allowed.
For the provided default ruleset, the rules are written so they do not overlap in any way that is consequential to the order they are in, so the default order is sufficient.
Updating Default Ruleset
The rules contained in a Ruleset are versioned so determining if a rule in your ruleset is out of date is simply a matter of looking at the rule’s detail and comparing it to the versions which may be found in the Lockdown Rules Release Notes.
The release notes detail which rules have been updated or added. Not all “releases” contain new rules but may be rules that have been rewritten for clarity or accuracy.
- To determine the version of a rule, navigate to the Control Policies | Policy Rules page, select the rule and its details will appear. The version number will be in the far-right corner.

- If a rule in your ruleset is out of date, you may download the latest ruleset json file from the Lockdown Rules Release Notes page to a folder on a system that has access to the ZMC portal.
- From the Actions drop-down on the Policy Rules page, select Upload New Rules.

- On the screen that appears, select the json file containing the updated lockdown rules.

- The upload process may take up to 5 minutes and there is no activity indicator.
- To verify the rules have updated, first review the release notes to know which rules have been updated or added then check that those rules reflect the changes. For ruleset additions, scroll to the bottom of the Policy Rules list and there will be a new rule set.

- As before, selecting the rule will open its details with the new version number.

Adding Recommended Ruleset to a Policy
Instead of adding individual rules, only the Recommended Ruleset is required. This ensures that the rules are added to a policy in the correct order to properly protect the endpoint system. An easy way to add the Recommended Ruleset to a policy is by the following steps:
- Create a Policy. Navigate to the Control Policies | Policies page. Once there select Add New Policy.

- On the New Policy pop-up menu, give your new policy a name and description. To add the recommended ruleset, click the Add Rules button.

- On the Policy Rules menu, scroll down the list of rules to Recommended Rules. Select this ruleset then click the Add Selected button.
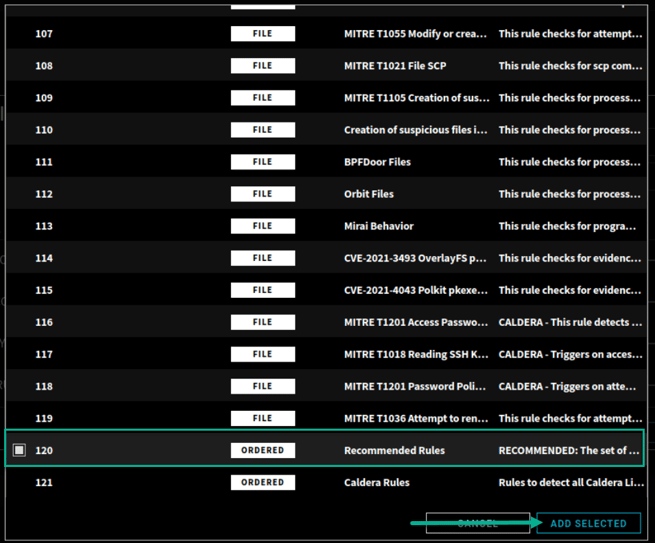
- On the screen that follows, your lockdown rules section will now include the Recommended Rules. Select CREATE on that screen.

- Once created, your new policy will appear in the Policies section.
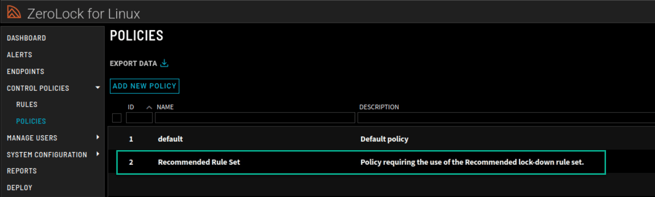
Applying a Policy to a Configuration Profile
In order to apply a policy to an endpoint, the policy must first be applied to a Configuration Profile.
- Navigate to the System Configuration | Config Profiles page and select Add New Profile.
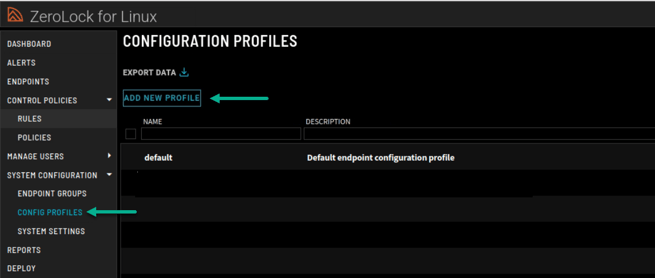
- On the New Configuration Profile pop-up menu, you can configure exactly what actions ZeroLock will take on each protection engine. Here, settings can be fine-tuned for Ransomware, Cryptojacking, and Tampering protection, as well as settings for all Hash Rules set to deny based on a SHA-256 hash (Blocking).

- In order to apply the policy that was created, navigate to the Default Control Policy drop-down menu, and select the preferred policy. Only one policy may be applied to a Configuration Profile at a time. Once complete, select the Create button at the bottom of the menu.

Applying a Configuration Profile to an Endpoint
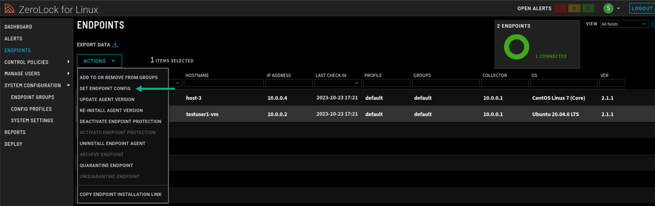
- Once a Configuration Profile has been created, it must be applied to an endpoint so the settings can take effect. Navigate to the Endpoints page.
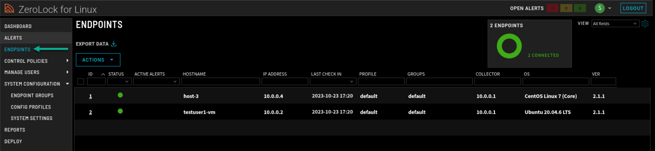
- On the Endpoints page, select the endpoint or multiple endpoints that you want to apply the new configuration profile to. Then, click the Actions drop-down menu and select Set Endpoint Config.
- On the Set Endpoint Configs pop-up menu, select the created configuration profile from the drop-down menu. Then select the Set Configs button.
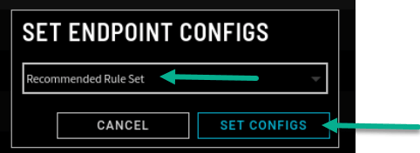
Your endpoints are now properly configured with the Recommended Ordered Ruleset.
