These release notes contain important information you should know before installing the ZeroLock® Platform so please familiarize yourself with all the new features listed in this document.
Downloading this release
To download the software, use this link to create a support request.
The ZeroLock Platform, has two components:
-
- ZeroLock Management Console (ZMC) v2.0.4
- ZeroLock Endpoint Agent (ZA) v2.1.4
System requirements and Installation Instructions
For more information on system requirements and installation instructions, see the knowledge base article:
New Features and Capabilities
NOTE: ZeroLock maintains the same efficacy and detection capabilities without internet or management console access. This capability is required for dark/air-gapped environments and certain embedded or IoT systems.
ZeroLock Management Console
Version 2.0.4 includes the following new features and capabilities:
Dashboard
Activity Log – Changes in Advanced Settings on the Deploy page are now more descriptive and easily understood.

Alerts and Rules
Automatic Allow Rule Generation - This enhancement allows for assisted rule generation when a false positive alert has been identified. Using this functionality, the user may quickly create an allow rule for the currently active alert thus reducing the possibility of clutter that can occur from unnecessary alerts. This functionality works for the predominant access alert types of File, Network, and Program access.
Alert Archiving - Within an active environment, endpoints will be added and deleted. This activity, along with testing and false positives, can result in cluttering up the Alerts table. With the User Permissions option, this clutter can now be easily cleared by archiving unnecessary alerts. On selection of an alert, or multiple alerts, to be archived, a caution dialog appears informing the user of the Alert ID numbers that will be archived and that it is not a recoverable action. Once archived, alerts are hidden from the Alerts and Dashboard activities pages.
Alerts Visible in Activities Log – The ZeroLock Management Console (ZMC) Dashboard has been updated to reflect a more verbose description of the alerts generated. When an alert is generated, the entries in the INFO column of the Activities Log include the endpoint ID number, the number of files affected and the ZeroLock response. For example, in response to a ransomware attack on protected Endpoint #1, the following appears in the Activities Log:
- E:1 – Killed attack on endpoint
- E:1 – 12 files affected
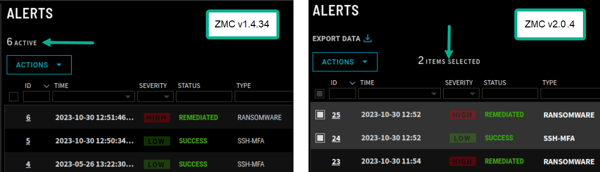
Alerts Counter – The counter for alerts has been modified for increased accuracy and clarity. Prior to this release, the ‘active’ alerts indicator showed the number of existing alerts, active and non-active. The updated indicator now shows the number of alerts that are selected as indicated by the white boxes next to the ID number of the alert.
Selective Remediation - This functionality occurs in the case where a customer is remediating an attack that, in addition to files affected by the attack, also contains legitimate changes from other processes in the tree. During a remediation event, the authorized user now has the option of specifying a list of files they would like to roll back to their pre-attack state while leaving all other files in their malware-modified state. After a remediation occurs, the files not selected are no longer recoverable.
Alert Enhancement - Alerts functionality enhanced to ensure an alert may only be remediated if it is in the “SUSPENDED” or “KILLED” state. When that alert is moved to either state, the list of impacted files is updated providing a complete list of files impacted. From this list, the user may then determine the files to be remediated.
Endpoints
Endpoint Archive Confirmation -To reduce the opportunity for inadvertent archival of an endpoint, a message asking for confirmation of the action now appears.
Advanced Settings – When deploying an Agent to an Endpoint, two (2) additional fields, with drop-down menus, have been added to this dialog box. The Endpoint Profile and Endpoint Groups fields, and their menus, enable the selection of the Configuration Profile for the endpoint and the endpoint groups to which it will belong.
ZeroLock Agent (ZA) Uninstallation Confirmation - When uninstalling a ZeroLock agent from an endpoint, a confirmation dialog containing the endpoint ID number is generated informing the user that the endpoint will no longer be protected by ZeroLock.
Endpoint Maintenance Tab Enhanced - The ability to easily copy the results using the ‘help’ and ‘get’ shortcuts has been added to the Endpoint Maintenance Tab. Now, copying the list of possible queries provided by the ‘help’ shortcut or the current endpoint configuration from the ‘get’ shortcut is a simple matter of clicking on the copy icon.
Endpoint Group – The options to Add or Remove an Endpoint from a group have been combined into a single entry under the ‘Actions’ dialog window.
Protection Availability Number/Counter - Individual endpoint’s Details page no longer displays the Protection Availability counter as had previous versions.
Agent Version Clarified – On the details page for an endpoint, ‘SW Version’ has been changed to ‘Agent Version’ to avoid possible confusion.
Queueing Added to Collector - To improve endpoint scalability, especially during potential high load times, queueing has been added to the Collector.
System Configuration Backup – The ability to enable/disable and schedule backup of the system configuration has been added. Backup scheduling options are Hourly, Daily, Weekly, and Monthly. The date and time format are mm/dd/yyyy and hh:mm (a|p)m.
Pagination – To provide enhanced utility, both the Alerts and Endpoints pages are now paginated instead of being infinite scrolls.
ZeroLock Agent
Version 2.1.4 includes the following new features and capabilities:
Performance – Agents and Endpoints
Agent enhanced to support the ‘Add Allow Rule’ capabilities - This enhancement allows for assisted rule generation when a false positive alert has been identified. Using this functionality, the user may quickly create an allow rule for the currently active alert thus reducing the possibility of clutter that can occur from unnecessary alerts. This functionality works for the predominant access alert types of File, Network, and Program access.
Agent enhancement enables protection of 32-bit applications running on 64-bit Linux distributions.
Collector Configuration Verification - To ensure that the Collector configuration has not been tampered with, when Tyr starts, the Collector List on the Endpoint is compared to the list from the ZeroLock service initially installed. If the lists do not match the ZeroLock service will not start.
Memory management enhancements were made that enable the Process Monitor to clear out memory of exited processes.
Enhanced Database Access - The number of database queries required to provide the Collector with the necessary Endpoint data has been reduced resulting in improving database access.
Improved Endpoint Agent Dependency Information - Having detailed information about all the dependencies used by the Endpoint agent can be critical. Recognizing this, the Baldur log now includes the fully qualified versions of an agent’s dependencies and any relevant additional information, such as the system’s architecture.
Syslog Reporting Functionality Enhancement - ZeroLock now supports writing logs to the local syslog on protected systems. This improvement allows you to obtain alert information through any of the SEIM/SOAR type solutions without necessarily having to write custom API integration for each one. The logs being updated with information are the /var/log/messages (centos/rh) or /var/log/auth.log (ubuntu). With this enhancement, and using native Linux syslog protocol functionality, our logging information can move to any log collector or consolidator.
Linux Distributions and curl - For some Linux distributions, curl is not included on the endpoint running the ZeroLock Endpoint Agent. To address this issue, the Re-Install Agent Version option will now use wget to do the reinstall if originally installed with wget.
Jumpbox Improvements - On protected endpoints running Jumpbox performance has been improved and false positives reduced.
Docker Containers - Several performance enhancements were made.
ZeroLock Endpoint Agent Shutdown - The agent shutdown process was adjusted so injected services will be restarted, Baldur detection engines will shut down, and ZeroLock service will be disabled.
Quarantine Improvement - A sync option has been added that refreshes configuration of the endpoint, preventing an endpoint from being reset into a quarantined state if suspended or rebooted.
Installation Enhancements
Improved installation for RHEL 8.8 STIG system – In STIG compliance, the cpio utility is responsible for extraction and digest validation of the files from rpm. This installer enhancement ensures installation stability and consistency by changing the packaging so that rpm digest will be sha256 while also adding support for RHEL STIG and other Linux distributions.
Agent installation enhanced to accept Configuration Profile and Endpoint Groups changes received from the Deploy page Advanced Settings configuration.
Improved installation support on non-Debian or non-rpm systems - Adding additional artifacts to the .tar package improved both the installation and uninstallation processes.
ZeroLock Container Agent now supports running with SELinux enabled on RHEL/Centos - The container-deployed agent is now allowed to install with SELinux enabled.
Alerts Enhancements
SSH MFA Alert - SSH-MFA alerts upgraded to be more precise.
Alert Remediation Information – To give the user more control and address any edge cases, only files that SHOULD NOT be remediated are listed. The user may select any additional files to be remediated from this list.
Behavior Analysis
Behavior analysis engine enhanced to update the path of a file when it is renamed to ensure restoration of all modified/deleted files when response type is set to ‘Suspend’.
Preventing ransomware corruption of /bin/bash program – The ZeroLock Agent’s Process Monitors receiving messages about the chmod system call family treat them as file writes for the purposes of tampering, lockdown rules, and file backup.
Logging Enhancement – Logging capabilities have been improved to help troubleshooting of endpoint issues, reducing time to resolution.
Enhanced Cache File Management – Improvements to non-zero threat value processes maintenance include the following:
- High Threat processes - with threat values above the designated threshold, data is kept for 14 days then cleaned up.
- Suspended processes - the process’s data is deleted, and the process is released.
- Exited processes - data associated with the process is deleted.
- Running processes - are not affected.
Detection Enhancement
Improved Program Execution Rule Enforcement – Program Execution rules that block a program now also prevent the renaming, copying, or moving of the program executable.
Program Execution Override – To make it easier to handle false positives, the system administrator is now allowed to add a Program Execution or File Access rule to override the behavior analysis engines when the process or file behavior has been verified good.
Cryptojacking Engine Improvement - Multiple enhancements to the Cryptojacking engine’s machine learning model have reduced false positives and improved its effectiveness.
Reduce False Positives from Cron Jobs - Performance improved and false positives reduced on protected endpoints running cron jobs.
Trademarks
ZeroLock and Vali Cyber are registered trademarks of Vali Cyber Inc. All other trademarks or service marks are property of their respected holders.
For information about the third-party software that is delivered with the product, refer to the third-party license file on your installation tar.gz that is specific to your release.
Legal Notice
The publication referencing this notice describes and/or represents products and services of Vali Cyber Inc. (“Vali”). It may contain trade secrets and proprietary information that are protected by various federal, state, and international laws, and distributed under licenses restricting their use, copying, modification, distribution, or transmittal in any form without prior written authorization of Vali. The publication is current as of the date of publication only. Changes to the publication may be made from time to time at the discretion of Vali. This publication remains the property of Vali. and must be returned to it upon request. The publication does not imply any commitment to offer or deliver the products or services described herein. The publication may include references to Vali product features that have not been licensed by you or your company. If you have questions about whether a particular capability is included in your installation, please consult your Vali services consultant. Although Vali strives for accuracy in its publications, any publication may contain inaccuracies or typographical errors, as well as technical inaccuracies. Vali shall not be liable for technical or editorial errors or omissions contained herein. Vali may make improvements and/or changes to the publication at any time without notice. Any references in the publication to non-Vali websites are provided for convenience only and do not serve as an endorsement of these websites. The materials at these websites are not part of the material for Vali products, and use of those websites is at your own risk. This publication may contain examples used in daily business operations that include the names of people, companies, products, and other third-party publications. Such examples are fictitious and any similarity to the names or other data used by an actual business enterprise or individual is coincidental.
This document is the property of:
Vali Cyber Inc.
529 Rookwood Place
Charlottesville, VA 22903
Feedback
If you have suggestions or comments for how we can improve our materials, send an email to: documentation@valicyber.com
