A guide for installing the ZeroLock® Agent onto the host OS of a Container Orchestration node.
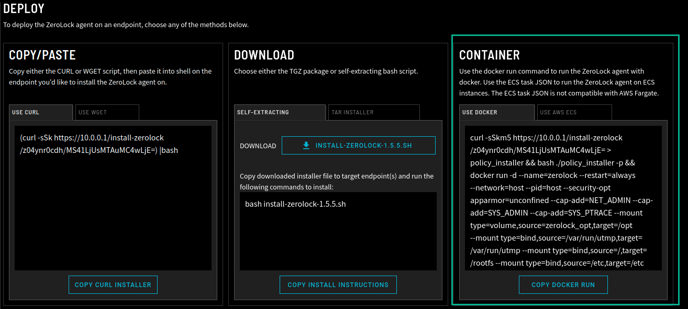
The ZeroLock® Agent (ZA) can be installed three (3) ways:
- COPY/PASTE – curl or wget
- DOWNLOAD – Self-Extracting bash or tar Installer
- CONTAINER – Docker or AWS ECS (instructions below)
Advanced Settings
Regardless of the installation method, there are settings that must be made prior to installing any agent. These Advanced Settings vary depending on the environment you are using and the agent version you intend to install.
On selecting an environment, the appropriate scripts are automatically included. For this example, select the Default environment and ensure that the Deploy – default screen is visible prior to proceeding with agent installation.
Use this link to access the settings guide: Advanced Settings
On configuring the Advanced Settings, you will be returned to the Deploy screen. Once there, select Use Docker tab in the Container group then the Copy Docker Run tab.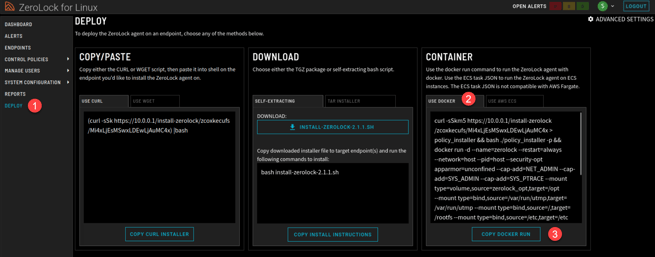
Endpoint Agent - Docker Container Installation
- Open a terminal window and connect to the endpoint.
- Ensure the latest version of Docker is installed.
- Run the command copied in step-3 above. (Depending on the user rights, you might need to run this command as sudo.)
Note: At this time, Podman is not supported.
Installation Example
Docker access is required to do the installation and run the container. You have two options:
- Make sure the user running the installer has the permissions required to run docker.
Or - You run the docker command with sudo. Once the command from step 3 is pasted into the terminal, insert sudo before ‘docker’ following an ampersand (&). This allows you to run the installation.
- Copy the command pasted into the terminal but DO NOT execute.

- Following an ampersand (&), insert sudo before docker, then execute.
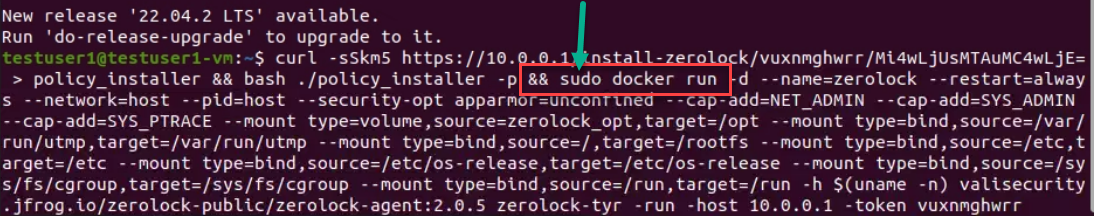
- Copy the command pasted into the terminal but DO NOT execute.
Validating Agent Installation
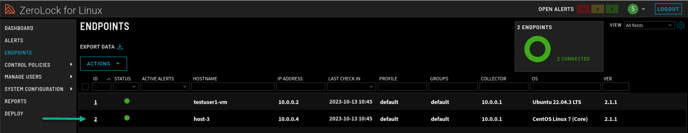
To validate the installation process, select the Endpoints tab on the main menu. The new endpoint will be listed. The green dot in the status column indicates a successfully installed agent on the endpoint system.
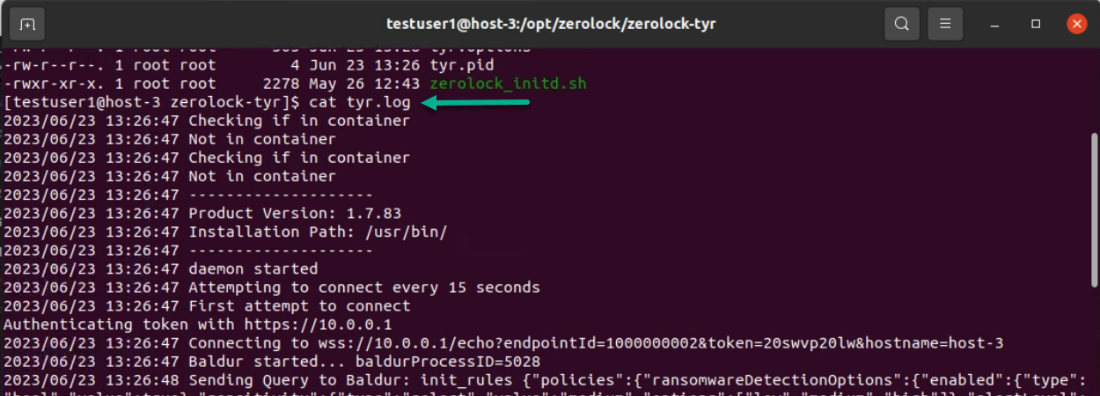
View ZeroLock® Agent Logs
Locate the ZeroLock® Agent logs.
cd /opt/zerolock/zerolock-tyr To go to the Tyr directory.
/opt/zerolock/zerolock-tyr$ ls -la To list the contents of the directory.

To see the ZeroLock® Agent log in detail, open a terminal session to the new Endpoint.
cat Tyr.log To read the log
Installation Options
The following are the available options that may be used during installation.
::: Vali Cyber ZeroLock Endpoint Software Installer (2.1.6) :::
Usage: ./installer [-h] [-n] [-v] [-x] [-p]
Options:
-h Print this help message and exit.
-n Perform a dry run, where no installation or changes are made. Useful for testing and debugging.
-v Output more information during installation. Useful for debugging and troubleshooting.
-x Perform troubleshooting steps for diagnosing problems.
-p Update the apparmor or selinux security profile or policy if additional permissions are required.
For more information, please see the Vali Cyber Support page.
